Today one can observe constant attacks against every public IP address. Most of the attacks are fully automatic and not targeted towards a specific victim. These kind of attacks don’t require much IT knowledge nor do they require a significant investment by the attacker as visualized in Figure 1.
On the next level one can find so called targeted attacks from cyber criminals or cyber activists such as “Anonymous” or “LulzSec“. The execution of targeted attacks requires some investment of the attacker into reconnaissance activities to create a profile of the victim, which for instance includes:
- employees
- supplying vendors
- relationships between identified entities (subjects and objects)
- IT equipment and software in use
- deployed defense capabilities and procedures
The gathered reconnaissance data is used to define the attack strategy. The manual process to collect, analyze and define an attack prevents (today) a fully automatic approach, which limits the number of attacks.
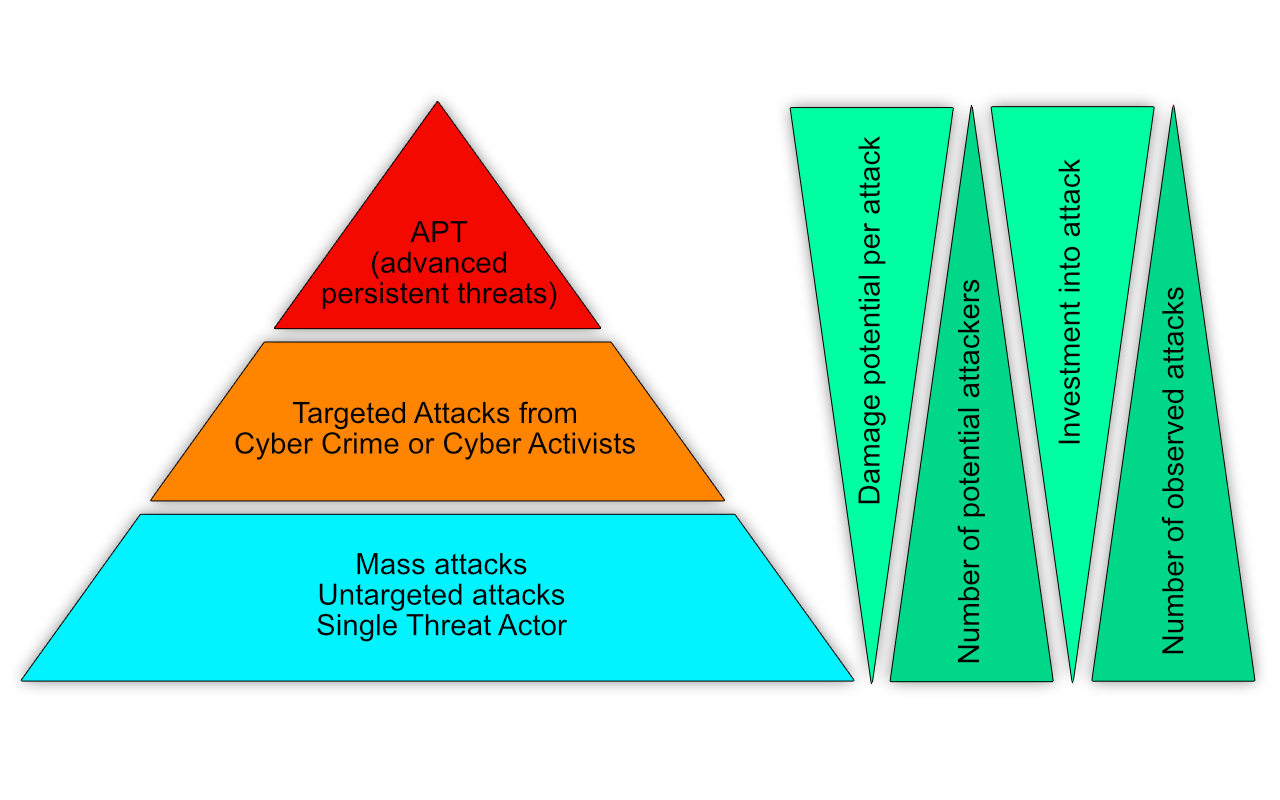
On top of the pyramid one can find the APT or “advanced persistent threat” class. These kind of attacks require a significant investment into the attack and a deep understanding of:
- networks
- communication protocols
- hard- and software
- detection, prevention and evasion methods
- psychology
Beside extensive reconnaissance activities the technology used during execution of the attack is tailored and created specially for the victim.
The amount of human resources available to be used for such attacks is limited and expensive. APT attacks try to be undetected as long as possible, so they try to hide within the “noise” of the victims daily operations, which causes these attacks to require often a long time (e.g. years) to be completed.
