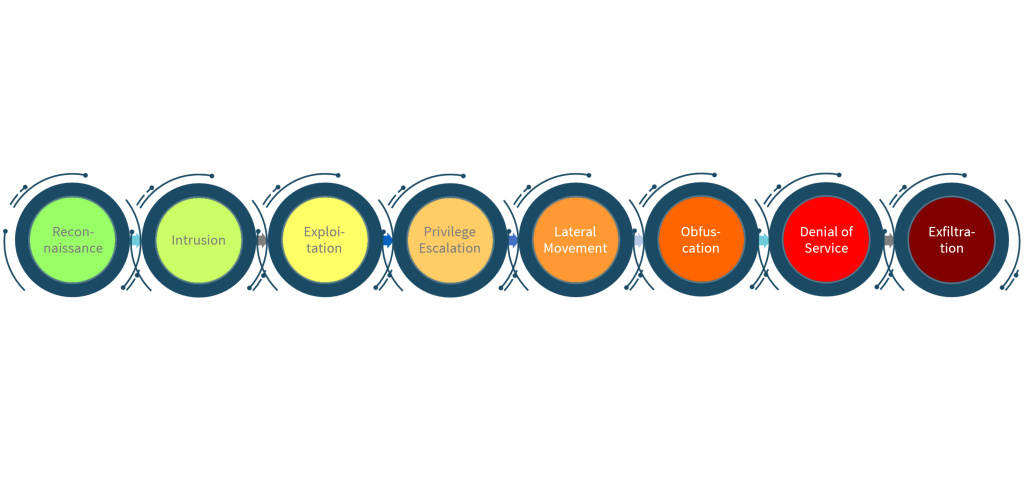
System Intrusion happens in an early phase of a cyber attack (Figure 1). It usually starts after attackers have collected enough data about the target and assembled tactics for their attack. The aim is to get initial access to the target. Detecting a cyber attack in this early stage is crucial to prevent increasing damage down the kill chain. The MITRE ATT&CK framework lists several attack techniques that can be detected during this phase, Phishing being one of them [1]. This Social Engineering attack is currently of the most common technique to gather credentials for direct access to systems, or to deploy malware for remote access. Other attack techniques include the exploit of public facing applications, and supply chain compromise.
Intrusion Detection
Intrusion detection systems (IDS) are used to detect attacks against a computer system or network at this early stage of the cyber killchain. To detect intrusion attempts, network traffic or hosts in the network are monitored for unusual traffic or suspicious activity. Possible incidents are identified, logged and alerts are raised. MITRE lists more than 20 attack techniques that can be mitigated by identifying them in this stage [2].
Intrusion detection differentiates mainly between host and network-based approaches. However, both approaches are usually combined in a hybrid way. Host-based approaches monitor log files, system activity, and system data in a centralized or distributed way. Network-based systems inspect the IP packages of network traffic.
Intrusion Prevention
While IDS are rather passive systems, Intrusion Prevention Systems (IPS) go one step further and automatically initiate prevention measures once a possible incident is identified.
Recommendation
IDS and IPS only protect your organization when they are well aligned with people, processes, and other technologies. Check if your organization is well equipped to detect cyber attacks at an early stage and prevent further damage:
- Are your IDS and IPS protected by special security measures?
- Are your IDS or IPS customized to monitor network and system activity properly?
- Are your IDS and IPS tested to effectively detect known threats?
- Are your IDS and IPS learning new attack patterns automatically?
- Do your IDS and IPS log and alert suspicious activity?
Need help to make the best of your IDS and IPS? Contact us for more information.
Sources
