The theft of credentials is one of today’s risks to Information Security that significantly increased with the rise of Social Engineering. Cyber criminals use credentials to intrude the infrastructure of organizations. They can then leverage this access to deal more damage.
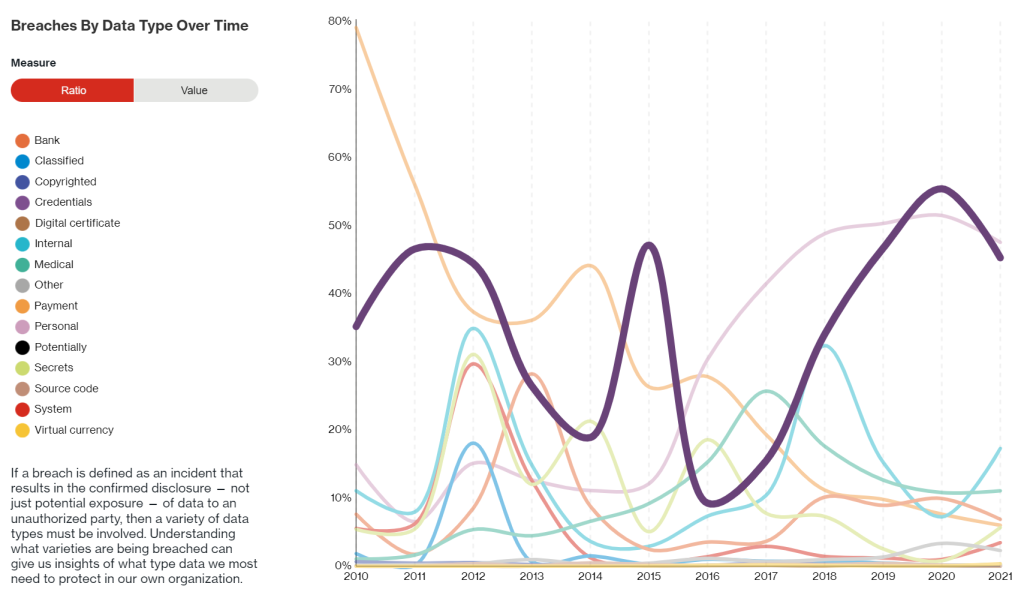
The interactive version of Verizon’s Data Breach Investigations Report (DBIR) illustrates that credentials were the #2 data type that led to data breaches in 2021. The usage of stolen credentials is one of the top attack vectors across espionage, financial, and other motives of cyber criminals [1].
Information Security Awareness
Organizations should train their employees to be aware of their responsibilities towards information security. Teaching employees to detect Social Engineering attempts like phishing or vishing will increase their protection from credential theft on a personal level.
Multi-Factor Authentication
Organizations, as well as employees as a private persons, should not rely on passwords as a single factor to authenticate a service or account. Instead, using a strong authentication involving two factors of different categories (e.g. a password plus an authentication token or a PIN plus a fingerprint) is highly recommended. This way a cyber criminal needs to circumvent an additional protection level even when he was able to steal credentials.
According to the Microsoft Digital Defense Report 2021, multi-factor authentication (MFA) prevents 99% of credential theft attacks [2]. However, the latest phishing campaign targeting Microsoft customers might put a damper on this statement [3].
Identity Threat Detection and Response
Organizations could reduce the attack surface for credential theft by safeguarding systems, accounts, and credentials with an identity threat detection and response (ITDR) solution. Highlighted as a 2022 trend by Gartner [4], these solutions can provide fake credentials on endpoint level and conceal real data. They can also provide detection abilities in case cyber criminals are already exploiting stolen credentials or misuse privileges. ITDR tools are especially helpful in organizations with a high number of non-human identities to manage.
Recommendation
Check if your organization is well prepared for credential theft:
- Are Cybersecurity awareness trainings regarding Social Engineering (e.g. test phishing mails) embedded in every employees daily work?
- Is a multi-factor authentication established for all critical accounts and services?
- Are your identities managed across on-premises and cloud assets, including users, applications, serverless functions, and containers?
Need help mitigating the risk of credential theft for your organization? Contact us for more information.
Sources
- [1] Verizon DBIR
- [2] Microsoft DDR
- [3] https://www.microsoft.com/security/blog/2022/07/12/from-cookie-theft-to-bec-attackers-use-aitm-phishing-sites-as-entry-point-to-further-financial-fraud/
- [4] https://www.gartner.com/en/newsroom/press-releases/2022-03-07-gartner-identifies-top-security-and-risk-management-trends-for-2022
