Are you sure your cyber security program is performing well?
We support you to test and asses your controls by simulating real world attacks on your people, technology and processes.
Penetration Testing is one of the most effective ways to identify security-relevant vulnerabilities in your system. It identifies unauthorized and/or malicious users, intrusion points and other potential compromises to your system’s integrity.The goal of penetration testing is to find all security relevant vulnerabilities in the inside the tested sytem.
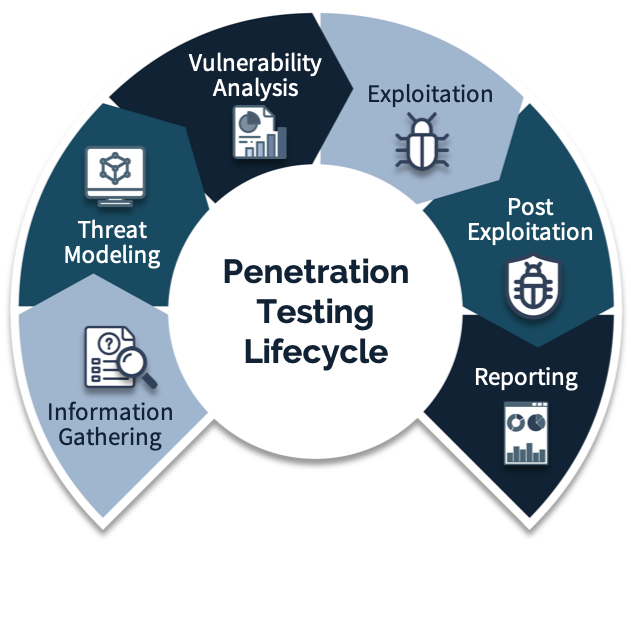 As with the process of Vulnerability Scanning, there are three types of Penetration Testing: 1. Black Box Testing, 2. White Box Testing and 3. Gray Box Testing. Nevertheless, there is a big difference between Vulnerability Scanning and Penetration Testing. Vulnerability Scanning is generally highly automated and aimed at detecting system vulnerabilities for the purpose of reporting to patch management. Penetration Testing, on the other hand, is often manual work, requiring detailed preparation in order to expose vulnerabilities. It is almost like a real attack, but conducted in a controlled environment in a deliberate and authorized manner in order to reveal the system’s weaknesses.
As with the process of Vulnerability Scanning, there are three types of Penetration Testing: 1. Black Box Testing, 2. White Box Testing and 3. Gray Box Testing. Nevertheless, there is a big difference between Vulnerability Scanning and Penetration Testing. Vulnerability Scanning is generally highly automated and aimed at detecting system vulnerabilities for the purpose of reporting to patch management. Penetration Testing, on the other hand, is often manual work, requiring detailed preparation in order to expose vulnerabilities. It is almost like a real attack, but conducted in a controlled environment in a deliberate and authorized manner in order to reveal the system’s weaknesses.
- Black Box Testing: the tester has no knowledge about the systems to be tested. He is responsible to collect information about the target network or system.
- White Box Testing: the tester is provided with complete information about the network and systems including the IP addresses, source codes, OS details, etc.
- Grey Box Testing: the tester is provided with partial knowledge of the system. This method mimics an attack by an external hacker who gains illegal access to network infrastructure documents.
In addition to the primary goal of detecting, Penetration Testing can be used to evaluate and asses the power of your Cyber Defense and the response time of your Incident Response Team.
Penetration Testing is complex, time consuming and requires a great deal of expertise.
We help you to define the scope of Penetration Testing in your company and support your testing and control assessment. We can safely simulate real-world cyber attacks on your personnel, technology and processes.
 Our team of specialists performs Penetration Tests as well as Red Team Testing to reveal your organization’s detection and response capabilities. Periodically performed Penetration Tests equip you to defend your organization against exploits.
Our team of specialists performs Penetration Tests as well as Red Team Testing to reveal your organization’s detection and response capabilities. Periodically performed Penetration Tests equip you to defend your organization against exploits.
